Defeat Malicious Contract Upgrades with WatchTower
How to monitor your favorite smart-contracts for malicious activity
In a perfect world, smart contracts are assumed to be immutable. However, most smart contracts are actually upgradeable, due to various practical reasons such as bug fixes and new features.
For example, Solana smart contracts can be modified and upgraded by default, and Ethereum smart contracts can be upgraded using a proxy such as TPP or UUPS.
What if your favorite (or dependent) smart contract is being upgraded w/o a prior notice, due to possibly a malicious attack, developers mistakes, or even the project team doing a rug pull?
WatchTower offers a ContractUpdateMonitor to monitor smart contract upgrades in real-time 7x24. Users will be alerted whenever a smart contract is upgraded regardless of the reasons. Moreover, WatchTower analyzes the upgraded code (e.g., rbpf or EVM byte codes) to flag if the code is potentially malicious (by checking common attack signatures).
In the rest of this article, we describe WatchTower ContractUpdateMonitor, and show in particular how it detects contract upgrades in real time on Solana.
Two main take-away messages:
Smart contracts may be upgradable unexpectedly due to mistakes and malicious behaviors
WatchTower offers a real-time threat monitor that can detect smart contract upgrades at any configured address and flag its risk using binary code analysis
What does a contract upgrade look like?
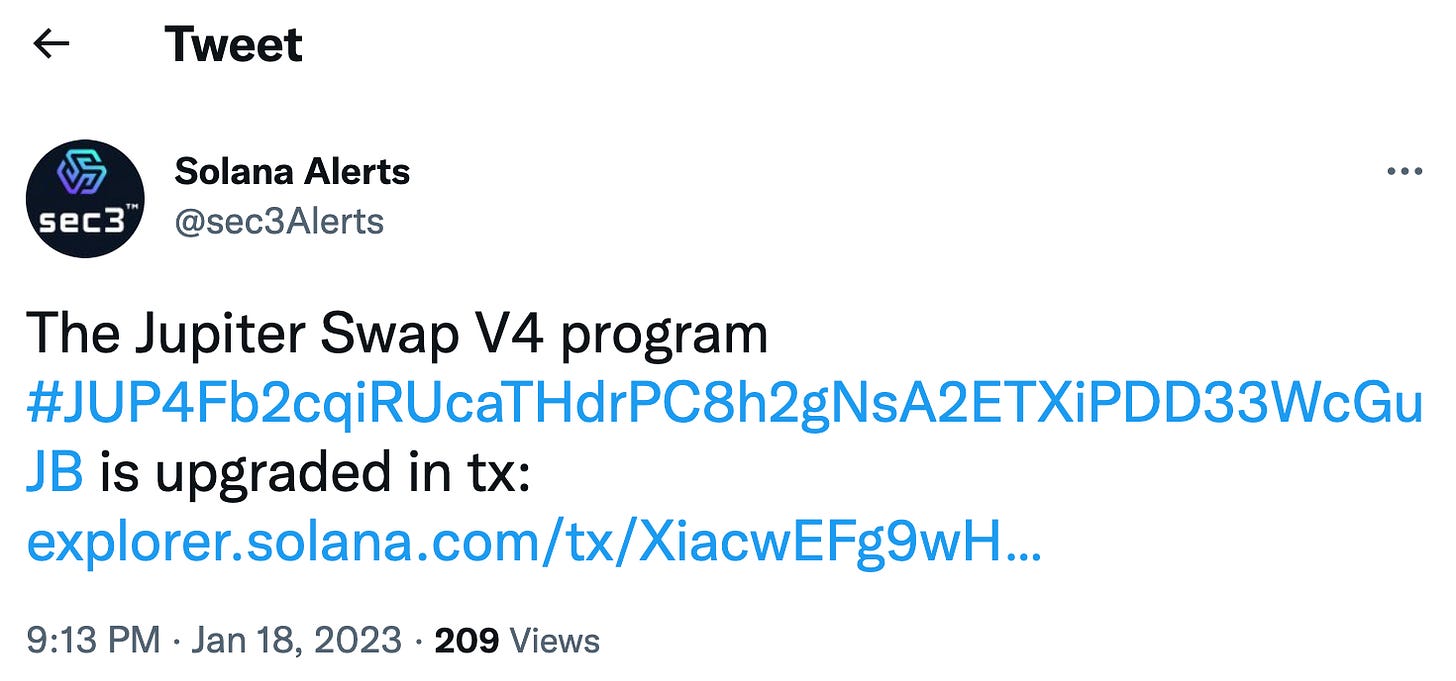
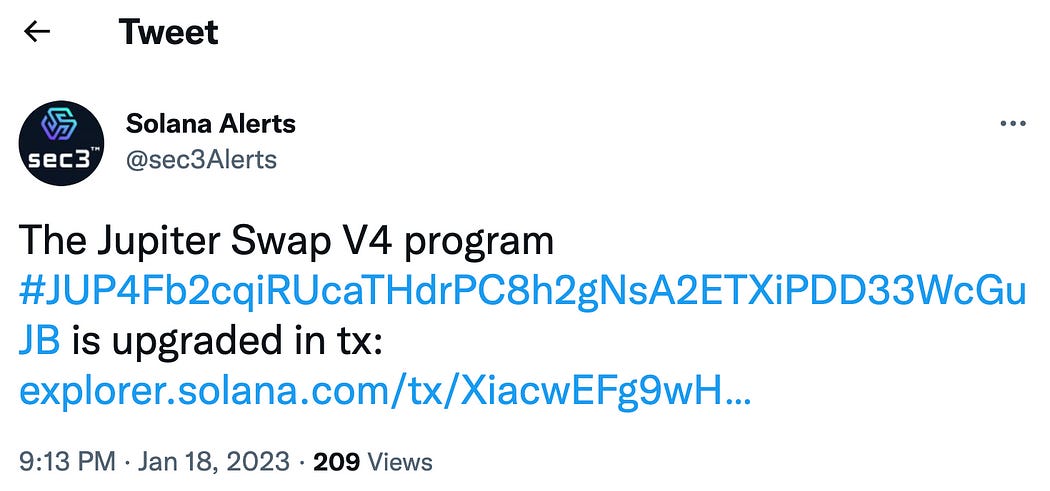
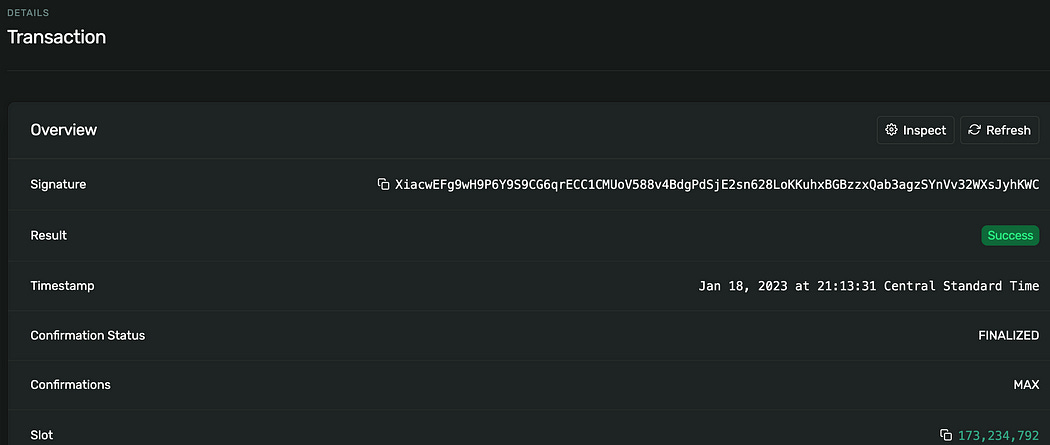
Figure 1 shows a tweet alert from @sec3Alerts on the Jupiter Swap V4 program upgrade. The explorer page of the transaction XiacwET shows the detailed transaction info:
It takes the BPF Upgradeable Loader program as the #13th input account:
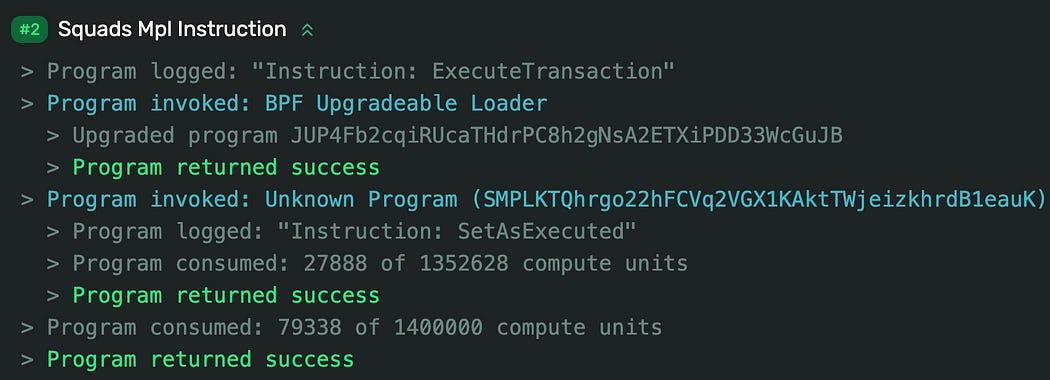
The program log also shows that BPF Upgradeable Loader is invoked to upgrade Jupiter Swap V4 (program_id: JUP4Fb2cqiRUcaTHdrPC8h2gNsA2ETXiPDD33WcGuJB):
The log above also reveals that the upgrade transaction was operated through a multisig instruction (Squads Mpl).
How does ContractUpdateMonitor work?
ContractUpdateMonitor inspects a few things in a transaction, including two main steps:
It traverses all the instructions (and nested instructions) to check if any instruction is an BPF Upgradeable Loader upgrade
If result of Step 1 is true, then it continues to check the input accounts and analyze the internals of the deployed binary code
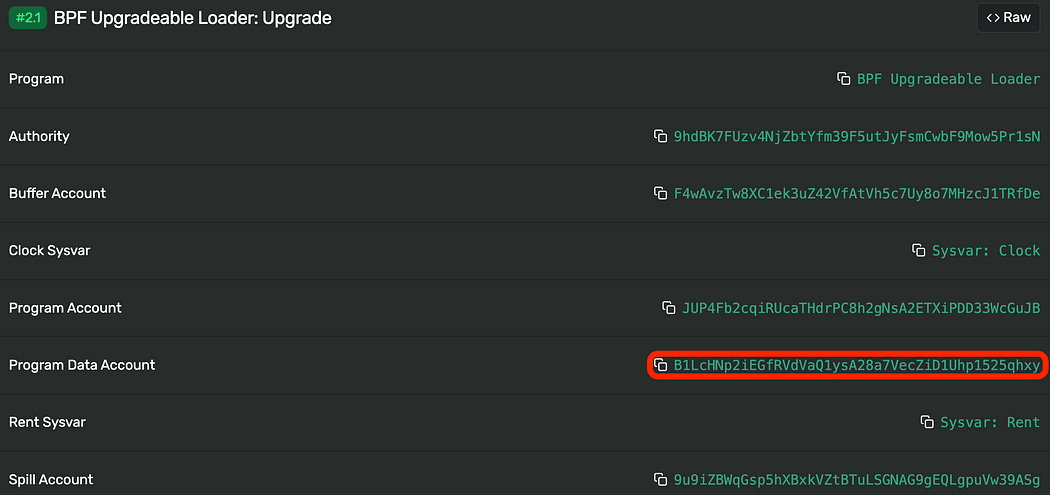
Figure 2 shows the format of input accounts of the BPF Upgradeable Loader upgrade instruction. The Program Account (#4) is the upgraded smart contract (program address).
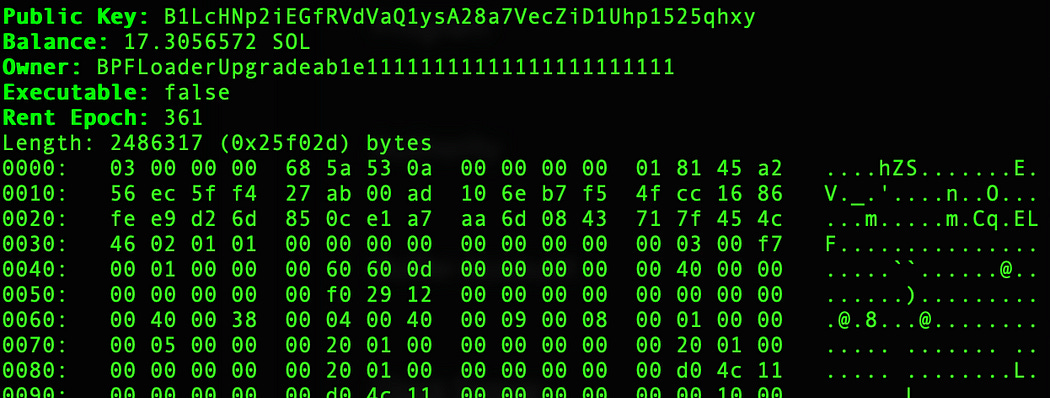
In particular, the Program Data Account (#5) contains the rbpf bytecodes:
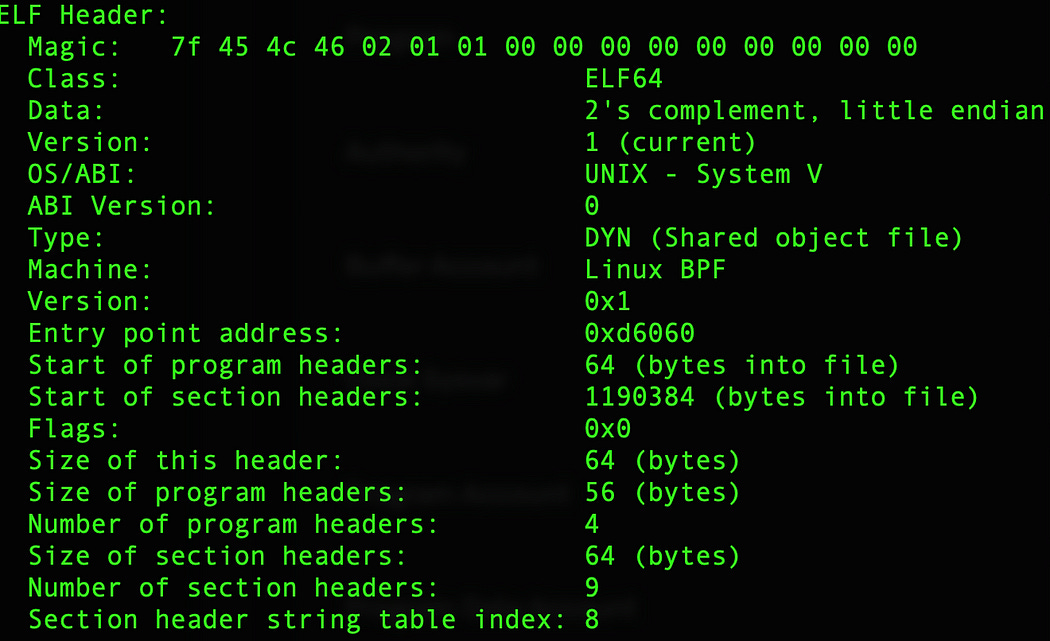
It is an ELF64 binary:
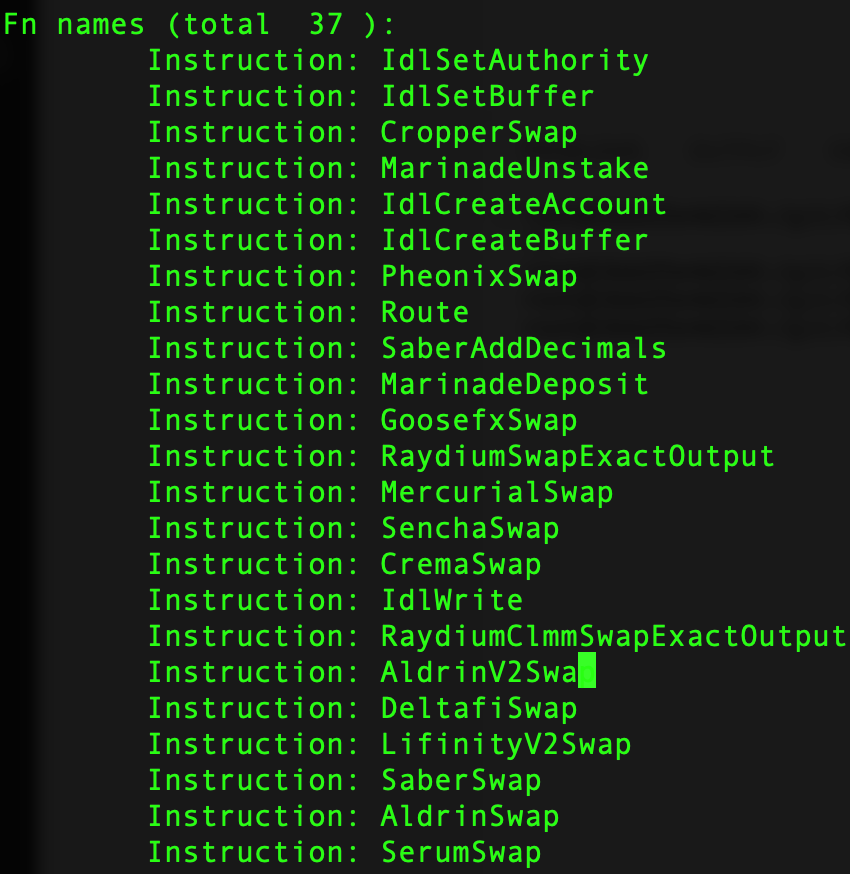
By analyzing the ELF64 binary, ContractUpdateMonitor checks if the code is potentially malicious (e.g., if it contains any know sequence of malicious instructions). For instance, a malicious binary often strips all symbols from object files and contains few functions.
The following shows a list of functions found in the upgraded Jupiter Swap V4 program binary, which is considered normal:
How to use ContractUpdateMonitor
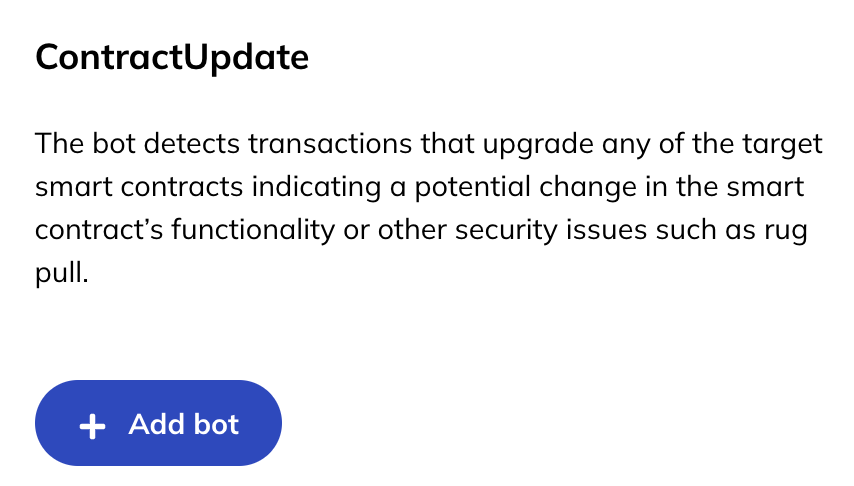
On the WatchTower dashboard, users can add a ContractUpdate bot:
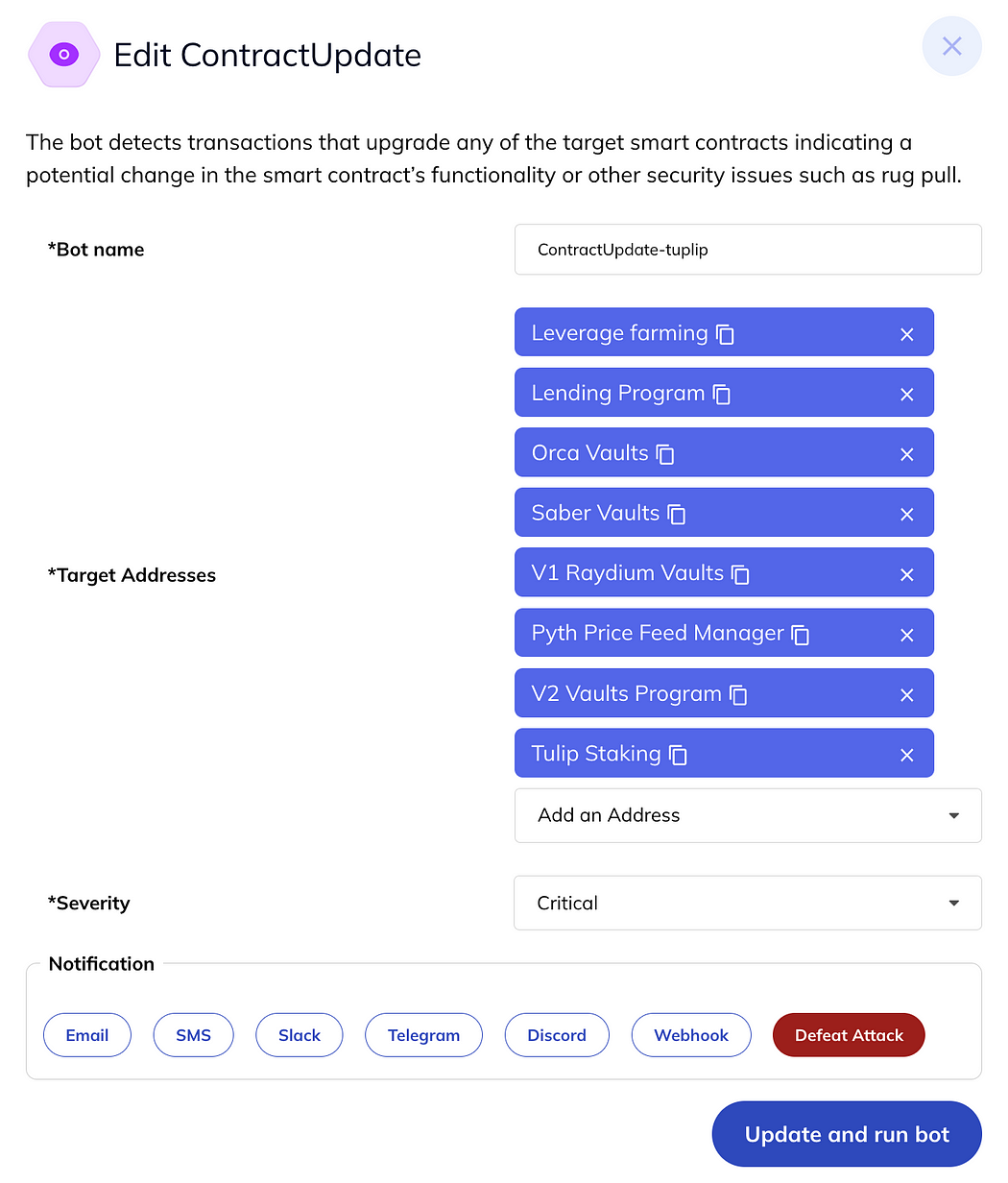
Click “Add bot” and configure the bot to monitor one or more target program addresses (i.e., smart contracts). The following shows a list of addresses for the Tulip project:
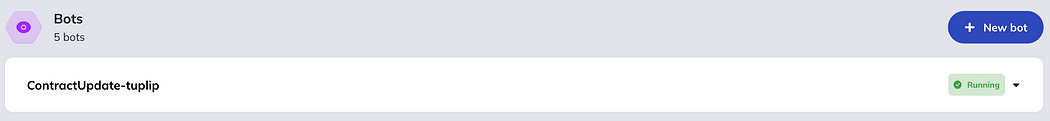
Once the bot is setup, it will be running 7x24:
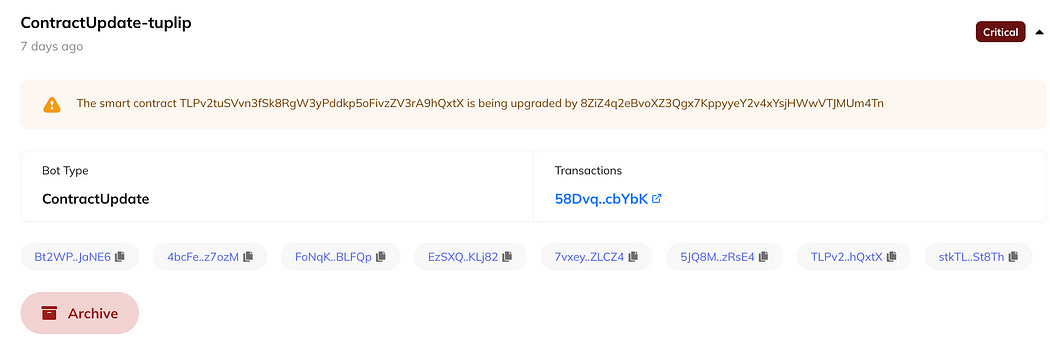
The bot will alert users in real-time upon a contract upgrade:
About Sec3 (formerly Soteria)
sec3 is a security research firm that prepares Solana projects for millions of users. sec3’s Launch Audit is a rigorous, researcher-led code examination that investigates and certifies mainnet-grade smart contracts; sec3’s continuous auditing software platform, X-ray, integrates with Github to progressively scan pull requests, helping projects fortify code before deployment; and sec3’s post-deployment security solution, WatchTower, ensures funds stay safe. sec3 is building technology-based scalable solutions for Web3 projects to ensure protocols stay safe as they scale.
To learn more about sec3, please visit: https://www.sec3.dev.